KringleCon 2
Kringlecon 2 - Holiday Hack Challenge 2019
Kringlecon 2 - Holiday Hack Challenge 2019
Introduction¶
Every year around the holidays SAN releases their CTF Holiday Hack challenge. These Holiday Hack challenges consists of a story and a mystery that revolve around the holidays and Santa.
As a player, you get to interact with a 2D world and work on solving challenges. Solving these challenges help players unravel the mystery of the holidays. As a result the players are put in a though spot to help Santa and save christmas.
This year's challenge is located at Elf university. There are 12 main objectives to solve in this year's challenge. The objectives have varying difficulty level, from 1 to 5 (easiest to hardest).
The players can receive hints for the main objectives by solving mini challenges called terminal challenges. As players solve each objective and terminal challenge, they receive badges.
As part of the holiday hack challenge, SANs releases a number of educational videos that may be helpful for solving the objectives.
This write-up will provide a walkthrough of the Holiday Hack Challenge. It includes a walkthrough of each objectives and terminal challenge. It will also provide inspiring quotes, hints and strategies on solving future challenges.
Links:
Protips¶
Kringlecon 2 - What You Can Do
My strategy for tackling each objective is as follow: - Solve the Terminal Challenges - Watch all the Videos - Tackle the Objective - Document and take screenshots as progressing through the game.
A tip from John Hammond to hold predominance over the universe:
Kringlecon 2 - The Infinity
The Pwn step is a function for the domain that you're trying to achieve predominance. It's a multidimensional thing.
There is a good series of tips by Katie Knowles in this conference. They can be watched here. Here is some keypoints of this talk:
Know your what and how!
Kringlecon 2 - How to Hack
How to Hack!
Kringlecon 2 - How to Hack
The problem spiral, which in some ways is the pwn step of the infinity
stonestep:
Kringlecon 2 - How to Hack!
Read this book!
Kringlecon 2 - Read this book before bed.
Holiday Hack Challenge Logo¶
If you're not feeling warm and fuzzy yet with your hot chocolate, don't worry you'll get there.
This year's logo looked interesting. Lets take a look at the logo.
Kringlecon 2 - ELF University Logo
There is latin on the logo Ille Te videt dum dormit.
Using google translator, it gives two different possible translation:
Ille Te videt dum dormit = We see him while he sleeps
Ille Te videt = He sees you
dum dormit = while sleeping
Then there is this all seeing eye on the logo.
Kringlecon 2 - Santa's All Seeing Eye?
Here are some of the rejected Logos:
Kringlecon 2 - 'rejected-elfu-logos.txt'
Hopefully you're feeling warm and fuzzy by now. Lets start the Holiday hack challenge!
Objective 0 - Talk to Santa in the Quad¶
| Inspirational Quote | "A positive attitude will help you and the world." -hacks4pancake |
| Objective | Enter the campus quad and talk to Santa. |
| Difficulty Level: | 0 |
| Links | n/a |
| Related Video | Lesley Carhart, Over 90,000: Ups and Downs of my InfoSec Twitter Journey |
Objective 0 - Walkthrough¶
As you enter the game you're greeted by Santa. He has the following message for you:
Kringlecon 2 - Santa at Entrance
Kringlecon 2 - Santa's Message
As you explore and enter the campus quad, you find Santa waiting there.
Kringlecon 2 - Santa in Campus
Objective 0 - Solution¶
Answer:
Talk to Santa in Campus.
He has the following message for you which starts the game:
Kringlecon 2 - Storyline
Objective 1 - Find the Turtle Doves¶
| Inspirational Quote | "In our hacker community, we're all family." -John Hammond |
| Objective | Find the missing turtle doves. |
| Difficulty Level: | 0 |
| Links | n/a |
| Related Video | John Hammond, 5 Steps to Build and Lead a Team of Holly Jolly Hackers |
Objective 1 - Walkthrough¶
As you walk and explore the campus you get to see the different areas you have access to.
Once you explore the student union, you will find the solution to this challenge.
Objective 1 - Solution¶
Answer:
Dove's are in the student union by the fireplace.
Kringlecon 2 - Michael and Jane - Two Turtle Doves
Very important message from the Doves:
Kringlecon 2 - Message from the Doves
Objective 2 - Unredact Threatening Document¶
| Inspirational Quote | "Pull That Thread." -Good Elf |
| Objective | Someone sent a threatening letter to Elf University. What is the first word in ALL CAPS in the subject line of the letter? Please find the letter in the Quad. |
| Difficulty Level: | 1 |
| Links | LetterToElfUPersonnel.pdf |
| Related Video | Heather Mahalik, When Malware Goes Mobile, Quick Detection is Critical |
Objective 2 - Walkthrough¶
As you walk around the quad and explore you find the following document in north west corner of the quad.
Kringlecon 2 - LetterToElfUPersonnel.pdf
As you open the document and examine it, you notice that you can highlight everything in the document.
Kringlecon 2 - LetterToElfUPersonnel.pdf content
You select everything and press 'CTRL-C' to copy everything.
You paste the content in a text editor to view the message:
Kringlecon 2 - LetterToElfUPersonnel.pdf content
Objective 2 - Solution¶
Answer:
DEMAND
Objective 3 - Windows Log Analysis: Evaluate Attack Outcome¶
| Inspirational Quote | " |
| Objective | We're seeing attacks against the Elf U domain! Using the event log data, identify the user account that the attacker compromised using a password spray attack. Bushy Evergreen is hanging out in the train station and may be able to help you out. |
| Difficulty Level: | 1 |
| Links | Security.evtx.zip |
| Related Video | Mark Baggett, Logs? Where we're going we don't need logs |
| Tools | SRUM-DUMP, ESE2CSV |
Escape Ed - Terminal Challenge¶
| Elf Name | Bushy Evergreen |
| Pre-Solve Hints | ed Editor Basics |
| Post-Solve Hints | Deep Blue CLI Posting, Deep Blue CLI on Github |
| Objective |
Kringlecon 2 - Escape Ed - Terminal Challenge
After you read the ed Editor Basics you find the solution for this terminal challenge.
Kringlecon 2 - Escape Ed - Terminal Challenge
Escape Ed - Solution¶
Kringlecon 2 - Escape Ed - Terminal Challenge
Answer:
Press q and press Enter.
Message from Bushy Evergreen after solving the challenge:
Kringlecon 2 - Objective 3 Hint
Objective 3 - Walkthrough¶
After you solve the terminal challenge, you learn about Deep Blue CLI.
You download Deep Blue CLI and run it against the 'security.evtx' file for the challenge.
Deep Blue CLI - Partial result of '.\DeepBlue.ps1 .\Security.evtx '
Deep Blue CLI - Partial result of '.\DeepBlue.ps1 .\Security.evtx '
When you view the Total Logon Failures, you quickly notice that all except one account have '77' failures. This may indicate that the account was authenticated successfully on the 77th attempt.
Objective 3 - Solution¶
Deep Blue CLI - Partial result of '.\DeepBlue.ps1 .\Security.evtx '
Answer:
supatree
Objective 4 - Windows Log Analysis: Determine Attacker Technique¶
| Inspirational Quote | "Go Hack it!" -kaknowles |
| Objective | Using these normalized Sysmon logs, identify the tool the attacker used to retrieve domain password hashes from the lsass.exe process. For hints on achieving this objective, please visit Hermey Hall and talk with SugarPlum Mary. |
| Difficulty Level: | 2 |
| Links | sysmon-data.json.zip |
| Related Video |
Linux Path - Terminal Challenge¶
| Elf Name | SugarPlum Mary |
| Pre-Solve Hints | Green words matter, files must be found, and the terminal's $PATH matters. |
| Post-Solve Hints | EQL Threat Hunting, Sysmon By Carlos Perez |
| Objective |
Kringlecon 2 - Linux Path
You open the terminal.
Kringlecon 2 - Linux Path Terminal
The objective is to get a listing of the current directory. You try the obvious solutions.
Kringlecon 2 - 'ls' and 'dir'
You remember the objective mentions that green words matter.
Kringlecon 2 - which ls
You try to find other programs that start with 'ls' .
Kringlecon 2 - locate '/ls/
You check the Path.
Kringlecon 2 - echo $PATH
You run '/bin/ls' to get dir listing.
Linux Path - Solution¶
Kringlecon 2 - '/bin/ls'
Kringlecon 2 - 'rejected-elfu-logos.txt'
Answer:
/bin/ls
Message from SugarPlum Mary after solving the challenge:
Kringlecon 2 - 'rejected-elfu-logos.txt'
Objective 4 - Walkthrough¶
You read the hints provided by SugarPlum Mary. You run the following three queries to solve this challenge:
Query 1:
$ eql query -f sysmon-data.json "process where process_name = 'lsass.exe'"
Query 1 gives you no results. You continue your journey with query 2.
Query 2:
$ eql query -f sysmon-data.json "process where parent_process_name = 'lsass.exe'" > results.json
You receive the following results from Query 2:
Kringlecon 2 - Query 2 results
You pivot on PID and run Query 3.
Query 3:
eql query -f sysmon-data.json "process where ppid = 3440" > results.json
You get the following result:
Kringlecon 2 - Query 3 results
Objective 4 - Solution¶
Answer:
ntdsutil
Objective 5 - Network Log Analysis: Determine Compromised System¶
| Inspirational Quote | "Tackle problems one step at a time. Take regular cocoa breaks!!" - kaknowles |
| Objective | The attacks don't stop! Can you help identify the IP address of the malware-infected system using these Zeek logs? For hints on achieving this objective, please visit the Laboratory and talk with Sparkle Redberry. |
| Difficulty Level: | 2 |
| Links | Zeek logs |
| Related Video | John Strand, Keynote: A Hunting We Must Go |
Xmas Cheer Laser - Terminal Challenge¶
| Elf Name | Sparkle Redberry |
| Pre-Solve Hints | SANS' PowerShell Cheat Sheet |
| Post-Solve Hints | RITA's homepage |
| Objective |
Kringlecon 2 - Xmas Cheer Laser - Terminal Challenge
You load the terminal for this challenge.
Kringlecon 2 - Xmas Cheer Laser - Terminal Challenge
You run the command (Invoke-WebRequest -Uri http://localhost:1225/).RawContent for more info.
Kringlecon 2 - Invoke-WebRequest -Uri http://localhost:1225/).RawContent
You do a directory listing to see what files are in the current directory. You read the callingcard.
Kringlecon 2 - Callingcard.txt
The calling card has references to history. You view the history.
Kringlecon 2 - 'history'
You notice Item 7 and 9 in history looks interesting.
You make a note of Item 7, (Invoke-WebRequest -Uri http://localhost:1225/api/angle?val=65.5).RawContent.
You're unable to read all of item 9, you dump history with all the properties.
Kringlecon 2 - riddle in history
You ponder on the riddle in the history item for a little while... You realize the riddle is referring to environment variables. You view the environment variables in the terminal.
Kringlecon 2 - Environment variables
You notice an environment variable named 'riddle'. You can't view the full content of the variable. You use out-string width 4096 to view more. You view the content of this environment variable.
Kringlecon 2 - Environment variables expanded
You compose a command line to search /etc recursively to look for the newest file that is likely compressed.
get-childitem -Path /etc –recurse -ErrorAction SilentlyContinue | where-object {$_.lastwritetime -gt (get-date).addDays(-1)} | where-object {-not $_.PSIsContainer} | Foreach-Object { $_.FullName + " " + $_.lastwritetime}
Kringlecon 2 - Riddle solution
You expand the 'archive' file using the command Expand-Archive -LiteralPath /etc/apt/archive -DestinationPath /home/elf/archive.
Kringlecon 2 - Expanding 'archive' file
You examine the content.
Kringlecon 2 - dir 'archive' file
Kringlecon 2 - dir 'archive' file
You find two files, another riddle and runme.elf.
You read the riddle.
Kringlecon 2 - riddle in 'archive' file
You have difficulty running the runme.elf. You google how to run elf file, you find the following article:
Kringlecon 2 - how to run 'elf' file
You try changing the attribute of the file prior to running it.
Kringlecon 2 - 'runme.elf'
You make a note of the refraction value.
You use the following powershell command to find a file with the specified md5 hash.
Get-ChildItem /home/elf -File -Recurse | Select DirectoryName,Name,@{N='Version';E={$_.VersionInfo.ProductVersion}},LastWriteTime,Length,@{N='FileHash';E={(Get-FileHash -Algorithm MD5 $_).Hash}} | select-string "25520151A320B5B0D21561F92C8F6224"
Kringlecon 2 - File with MD5 hash "25520151A320B5B0D21561F92C8F6224"
You view this file.
Kringlecon 2 - Another riddle
You make a note of the temperature. You find another riddle in this file.
You create the following powershell command to solve the riddle:
get-childitem -Path /home/elf/depths/ –recurse -ErrorAction SilentlyContinue | Foreach-Object { $_.FullName } | sort { $_.length } |
The results are as follow:
Kringlecon 2 - Riddle solution
Kringlecon 2 - Yet another riddle.
You use the following powershell command to solve the above riddle.
Get-Process -IncludeUserName | Select-Object Id,Name,Username,Path
Stop-Process -ID 23 -Force
Stop-Process -ID 26 -Force
Stop-Process -ID 27 -Force
Stop-Process -ID 29 -Force
Kringlecon 2 - Yet another riddle.
You do a dir listing of /shall to find another riddle. You use the following powershell command to solve this riddle.
get-childitem -Path /etc *.xml –recurse -ErrorAction SilentlyContinue
Kringlecon 2 - Riddle solution
You ponder on how to this. After a while you try the following command:
type /etc/systemd/system/timers.target.wants/EventLog.xml | Select-String "<I32 N=""Id"">" | Group-Object
Kringlecon 2 - lonely event id
You use the following powershell command to get the properties of the lonely event id.
type /etc/systemd/system/timers.target.wants/EventLog.xml | Select-String "<I32 N=""Id"">1</I32>" -Context 1,150
Kringlecon 2 -'$correct_gases_postbody'
You make a note of the correct gases.
Now you have the temperature, angle, gas composition, refraction value. You set the correct parameters on the laser.
Xmas Cheer Laser - Solution¶
Answer:
(Invoke-WebRequest -Uri http://localhost:1225/api/off).RawContent
(Invoke-WebRequest -Uri http://localhost:1225/api/refraction?val=1.867).RawContent
(Invoke-WebRequest -Uri http://localhost:1225/api/temperature?val=-33.5).RawContent
(Invoke-WebRequest -Uri http://localhost:1225/api/angle?val=65.5).RawContent
$correct_gases_postbody = "O=6&H=7&He=3&N=4&Ne=22&Ar=11&Xe=10&F=20&Kr=8&Rn=9"
Invoke-WebRequest -Uri http://localhost:1225/api/gas -Method POST -Body $correct_gases_postbody
(Invoke-WebRequest -Uri http://localhost:1225/api/on).RawContent
Xmas Cheer Laser - Solution
Message from Sparkle Redberry after solving the challenge:
Xmas Cheer Laser - Solution
Objective 5 - Walkthrough¶
You read the Rita hint from the terminal challenge and watch the related video. You're now a RITA expert!
You extract the Zeek files provided in this challenge. You view the RITA output.
You view the Beacons:
RITA - Beacons
Objective 5 - Solution¶
Answer:
144.202.46.214
Objective 6 - Splunk¶
| Inspirational Quote | "Set boundaries (time, abuse, triggers, requests, pancakes...)" -hacks4pancake |
| Objective | Access https://splunk.elfu.org/ as elf with password elfsocks. What was the message for Kent that the adversary embedded in this attack? The SOC folks at that link will help you along! For hints on achieving this objective, please visit the Laboratory in Hermey Hall and talk with Prof. Banas. |
| Difficulty Level: | 3 |
| Links | https://splunk.elfu.org/ |
| Related Video | James Brodsky, Dashing Through the Logs |
Splunk Training Questions - Terminal Challenge¶
| Elf Name | Professor Banas |
| Objective |
Kringlecon 2 - Splunk Training
You proceed to login to https://splunk.elfu.org/ wither username elf/Password:elfsocks.
Once you log in, you're greeted with the following messages:
Kringlecon 2 - https://splunk.elfu.org/ welcome page
Kringlecon 2 - https://splunk.elfu.org/ ELF University SOC
The various Chats will help you answer the training questions and the challenge questions.
Here is the list of the questions:
Question 1:
What is the short host name of Professor Banas' computer?
Question 2:
What is the name of the sensitive file that was likely accessed and copied by the attacker? Please provide the fully qualified location of the file. (Example: C:\temp\report.pdf)
Question 3:
What is the fully-qualified domain name(FQDN) of the command and control(C2) server? (Example: badguy.baddies.com)
Question 4:
What document is involved with launching the malicious PowerShell code? Please provide just the filename. (Example: results.txt)
Question 5:
How many unique email addresses were used to send Holiday Cheer essays to Professor Banas? Please provide the numeric value. (Example: 1)
Question 6:
What was the password for the zip archive that contained the suspicious file?
You work with the users in SOC to answer these questions. They walk you through answering each question. You read the chat and perform the searches, review the results to answer the questions.
For question 1 you review #ELFU SOC chat log.
For question 2, you search index=main santa and review the results.
For question 3, you search for index=main sourcetype=XmlWinEventLog:Microsoft-Windows-Sysmon/Operational powershell EventCode=3
For question 4, you search for index=main sourcetype=WinEventLog EventCode=4688 | reverse and review the events.
For question 5, you search for index=main sourcetype=stoq | table _time results{}.workers.smtp.to results{}.workers.smtp.from results{}.workers.smtp.subject results{}.workers.smtp.body | search results{}.workers.smtp.subject="*Holiday
Cheer Assignment Submission*" results{}.workers.smtp.to="*carl*"
For question 6, you can find the password in the malicious email carl received in question 5.
Splunk Training Questions - Solution¶
Kringlecon 2 - Training Questions/Answers
Answer:
Training Questions
1. sweetums
2. C:\Users\cbanas\Documents\Naughty_and_Nice_2019_draft.txt
3. 144.202.46.214.vultr.com
4. 19th Century Holiday Cheer Assignment.docm
5. 21
6. 123456789
7. Bradly.Buttercups@eIfu.org
Objective 6 - Walkthrough¶
Challenge Question:
What was the message for Kent that the adversary embedded in this attack?
Kringlecon 2 - List of interesting files
You will use the following splunk search get a list of files that may contain the message for Kent:
index=main sourcetype=stoq "results{}.workers.smtp.from"="bradly buttercups <bradly.buttercups@eifu.org>"
| eval results = spath(_raw, "results{}")
| mvexpand results
| eval path=spath(results, "archivers.filedir.path"), filename=spath(results, "payload_meta.extra_data.filename"), fullpath=path."/".filename
| search fullpath!=""
| table filename,fullpath
You will get the following results:
Kringlecon 2 - Files
Looking at the malicious file you get the following message:
Kringlecon 2 - malicious file
You try a different file and see the following:
Kringlecon 2 - xml file
Objective 6 - Solution¶
Answer:
Kent you are so unfair. And we were going to make you the king of the Winter Carnival.
Kringlecon 2 - Challenge Answer
Kringlecon 2 - Challenge Answer
Objective 7 - Get Access To The Steam Tunnels¶
| Inspirational Quote | "Deep breath, Loook at the data!" - Random Math Professor standing behind you |
| Objective | Gain access to the steam tunnels. Who took the turtle doves? Please tell us their first and last name. For hints on achieving this objective, please visit Minty's dorm room and talk with Minty Candy Cane. |
| Difficulty Level: | 3 |
| Links | Key Decoding |
| Related Video | Deviant Ollam, Optical Decoding of Keys |
Prior to accessing the terminal challenge we need to unlock the dorm room.
Frosty Keypad Challenge¶
Here is the keypad to access the dorm room:
Kringlecon 2 - Frosty Keypad
The Elf Tangle Coalbox by the dorm door gives you the following hints:
Kringlecon 2 - Elf Tangle Coalbox
Kringlecon 2 - Frosty Keypad Hints
From the keypad and the hints you can tell the three keys in the code are '1', '3' and '7'.
You write the following python function to find all the 4 digit prime numbers with only the digits '1', '3', '7'.
# prime function from https://stackoverflow.com/questions/15285534/isprime-function-for-python-language
def is_prime(n):
if n == 2 or n == 3: return True
if n < 2 or n%2 == 0: return False
if n < 9: return True
if n%3 == 0: return False
r = int(n**0.5)
f = 5
while f <= r:
#print ('\t',f)
if n%f == 0: return False
if n%(f+2) == 0: return False
f +=6
return True
# Program to check if a number is prime or not
# for number in range(1000:10000)
for number in range(1000,10000):
x = str(number)
#print(x + ' is Prime.')
if (x.find('1')>-1 and x.find('3')>-1 and x.find('7')>-1):
if (x.find('0')== -1 and x.find('2')== -1 and x.find('4')== -1 and x.find('5')== -1 and x.find('6')== -1 and x.find('8')== -1 and x.find('9')== -1):
if is_prime(number):
print(x + ' is Prime.')
Here are the result of the above program:
Kringlecon 2 - Frosty Keypad Possible Combinations
Frosty Keypad - Solution¶
You try all the above combinations and find the correct combination is 7331. Once you enter the dorm room, you notice that the combination is written on the wall.
Kringlecon 2 - Dorm Room - Bad Security
Holiday Hack Trial - Terminal Challenge¶
| Elf Name | Misty CandyCane |
| Pre-Solve Hints | Web Apps: A Trailhead |
| Post-Solve Hints | Deviant's Key Decoding Templates,Optical Decoding of Keys |
| Objective |
Kringlecon 2 - Minty Candycane
The game has 3 difficulty levels. You notice a URL on top of the game page.
Kringlecon 2 - Holiday Hack Trail - Terminal Challenge
Easy mode¶
You select the EASY mode. You notice the URL on top of the game has changed.
Kringlecon 2 - Easy mode
You copy and paste the URI to a text editor:
hhc://trail.hhc/trail/?difficulty=0&distance=0&money=3600&pace=0&curmonth=7&curday=1&reindeer=4&runners=4&ammo=100&meds=20&food=400&name0=Anna&health0=100&cond0=0&causeofdeath0=&deathday0=0&deathmonth0=0&name1=Michael&health1=100&cond1=0&causeofdeath1=&deathday1=0&deathmonth1=0&name2=Billy&health2=100&cond2=0&causeofdeath2=&deathday2=0&deathmonth2=0&name3=Vlad&health3=100&cond3=0&causeofdeath3=&deathday3=0&deathmonth3=0
You update the distance variable in the URL to 8000 and press the >.
You press the Go button and you get the following message:
Kringlecon 2 - Terminal Challenge Solved
Medium mode¶
You start the game again on Medium difficulty. You notice the URL bar has changed. You no longer can modify the variables in the URL to win.
Kringlecon 2 - Medium mode
You inspect the elements on the page and find a div 'statusContainer' that contains hidden variables.
Kringlecon 2 - statusContainer
You modify the distance variable to 8000 and press "Go".
Kringlecon 2 - distance variable
Hard mode¶
You start the game in hard difficulty mode.
The solutions for the last two mode no longer work. You examine the 'statusContainer and notice now it contains a hash value.
Kringlecon 2 - hash
You type the hash in Crackstation.
You get the following result:
Kringlecon 2 - md5 hash
The hash 6da9003b743b65f4c0ccd295cc484e57 is a md5 hash for 230.
After playing around with the game for a while, you notice the hash is calculated by adding all the values together. The Values added are money, distance, curmonth, curday, runners,reindeer, ammo, meds, food.
You restart the game. You add calculate the md5 hash of (8000+230). You use CyberChef to calculate the hash. The hash is bd4a6d0563e0604510989eb8f9ff71f5
You update the distance to 8000 and hash to the above and press Go.
Holiday Hack Trial - Solution¶
Answer:
Easy:
hhc://trail.hhc/trail/?difficulty=0&distance=8000&money=3600&pace=0&curmonth=7&curday=1&reindeer=4&runners=4&ammo=100&meds=20&food=400&name0=Anna&health0=100&cond0=0&causeofdeath0=&deathday0=0&deathmonth0=0&name1=Michael&health1=100&cond1=0&causeofdeath1=&deathday1=0&deathmonth1=0&name2=Billy&health2=100&cond2=0&causeofdeath2=&deathday2=0&deathmonth2=0&name3=Vlad&health3=100&cond3=0&causeofdeath3=&deathday3=0&deathmonth3=0
Medium:
Modify the distance variable in div "statusContainer" to 8000 and press "Go".
Hard:
You use the same solution as Medium, except you update the hash.
The hash is md5(sum(money, distance, curmonth, curday, runners,reindeer, ammo, meds, food))
Message from Minty Candycane after solving the challenge:
Kringlecon 2 - Minty Candycane - Terminal Challenge
Objective 7 - Walkthrough¶
You watch the video for this challenge. You review the elements on the page and notice a class called "krampus scampering".
Kringlecon 2 - "krampus scampering"
You open the image mentioned in the krampus class in your browser.

Kringlecon 2 - krampus.png
You cut the key image and rotate it.

Kringlecon 2 - krampus's key
You have two options, use the templates provided for the challange or try to eyeball it.
You decide to eyeball it.
You trying the following combinations
133430
133530
133630
133730
233530
122420
122520(answer)
The door opens up with 122520 key.
Kringlecon 2 - Door opened by key `122520`
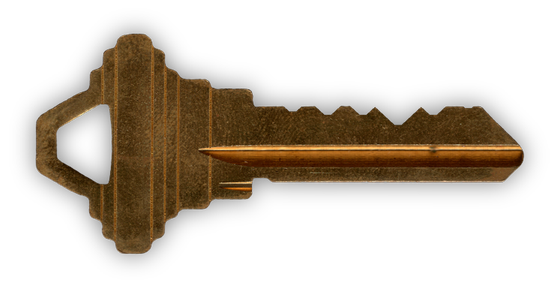
Kringlecon 2 - Key `122520`
You through the door and down the steam tunnel. You reach the end of the steam tunnel.

Kringlecon 2 - Krampus / Frido Sleigh Contest
Kringlecon 2 - Krampus Hollyfeld
Objective 7 - Solution¶
Answer:
Krampus Hollyfeld
Objective 8 - Bypassing the Frido Sleigh CAPTEHA¶
| Inspirational Quote | "Being devious is half of the fun!" -kaknowles |
| Objective | Help Krampus beat the Frido Sleigh contest. For hints on achieving this objective, please talk with Alabaster Snowball in the Speaker Unpreparedness Room. |
| Difficulty Level: | 4 |
| Links | Frido Sleigh contest, 12,000 images, API interface |
| Related Video | Chris Davis, Machine Learning Use Cases for Cybersecurity |
Nyanshell - Terminal Challenge¶
| Elf Name | Alabaster Snowball |
| Pre-Solve Hints | On Linux, a user's shell is determined by the contents of /etc/passwd, sudo -l says I can run a command as root. What does it do? |
| Post-Solve Hints | Chris Davis, Machine Learning Use Cases for Cybersecurity |
| Objective |
You arrive in the Speaker Unpreparedness Room.
Kringlecon 2 - Speaker Unpreparedness Room
You talk to Alabaster Snowball.
Kringlecon 2 - Alabaster Snowball - Terminal Challenge
You open the Nyanshell.
Kringlecon 2 - Nyanshell - Terminal Challenge
You run sudo -l to see the list of files you can and can't run with sudo permission.
Kringlecon 2 - sudo -l
Kringlecon 2 - /etc/passwd
You look around in different folders, and you find a file /entrypoint.sh
Kringlecon 2 - entrypoint.sh
You try running entrypoint.sh. You check the attribute of /bin/nsh using lsattr /bin/nsh command. You notice /bin/nsh is marked as immutable.
Kringlecon 2 - getting attribute of /bin/nsh
You change this attribute by using sudo chattr -i /bin/nsh command. You copy /bin/bash over /bin/nsh
Kringlecon 2 - changing nsh from immutable to mutable
You login as alabaster_snowball with the username provided on loading of the terminal (alabaster_snowball/Password2).
Kringlecon 2 - su alabaster_snowball
You run the success script after.
Kringlecon 2 - running the success script
Kringlecon 2 - nyancat
Nyanshell - Solution¶
Answer:
sudo chattr -i /bin/nsh
cp /bin/bash /bin/nsh
su alabaster_snowball with password: "Password2"
Message from Alabaster Snowball after solving the challenge:
Kringlecon 2 - Nyanshell solved
Objective 8 - Walkthrough¶
You view the website for the contest, Frido Sleigh contest. The website has a complex captcha puzzle.
Kringlecon 2 - Contest Captcha
You watch the related video for this objective. You download all the related files for this section.
You download the repository from the video img_rec_tf_ml_demo.
You follow the instructions on the img_rec_tf_ml_demo github page to install Tensorflow:
Kringlecon 2 - TensorFlow installation
You run the demo to ensure you get the coprrect results.
Kringlecon 2 - TensorFlow Demo
You download capteha_api.py file and copy it to the demo tensorflow folder.
You extract the 12,000 images you downloaded by running the following commands:
mkdir training_images
tar xvzf capteha_images.tar.gz -C ./training_images
You remove the demo model training files, rm -r /tmp/retrain_tmp/.
You retrain with model with the capteha_images.
Kringlecon 2 - Training Model 1/2
Kringlecon 2 - Training Model 2/2
You review capteha_api.py and predict_images_using_trained_model.py from the tensorflow demo.
You add capteha_api.py to predict_images_using_trained_model.py file.
You write the code the extra code to use ML model to solve the captcha.
#!/usr/bin/python3
# Image Recognition Using Tensorflow Exmaple.
# Code based on example at:
# https://raw.githubusercontent.com/tensorflow/tensorflow/master/tensorflow/examples/label_image/label_image.py
import os
os.environ['TF_CPP_MIN_LOG_LEVEL'] = '3'
import tensorflow as tf
tf.logging.set_verbosity(tf.logging.ERROR)
import numpy as np
import threading
import queue
import time
import sys
import requests
import json
import base64
from array import *
# sudo apt install python3-pip
# sudo python3 -m pip install --upgrade pip
# sudo python3 -m pip install --upgrade setuptools
# sudo python3 -m pip install --upgrade tensorflow==1.15
def load_labels(label_file):
label = []
proto_as_ascii_lines = tf.gfile.GFile(label_file).readlines()
for l in proto_as_ascii_lines:
label.append(l.rstrip())
return label
def predict_image(q, sess, graph, image_bytes, img_full_path, labels, input_operation, output_operation):
image = read_tensor_from_image_bytes(image_bytes)
results = sess.run(output_operation.outputs[0], {
input_operation.outputs[0]: image
})
results = np.squeeze(results)
prediction = results.argsort()[-5:][::-1][0]
q.put( {'img_full_path':img_full_path, 'prediction':labels[prediction].title(), 'percent':results[prediction]} )
def load_graph(model_file):
graph = tf.Graph()
graph_def = tf.GraphDef()
with open(model_file, "rb") as f:
graph_def.ParseFromString(f.read())
with graph.as_default():
tf.import_graph_def(graph_def)
return graph
def read_tensor_from_image_bytes(imagebytes, input_height=299, input_width=299, input_mean=0, input_std=255):
image_reader = tf.image.decode_png( imagebytes, channels=3, name="png_reader")
float_caster = tf.cast(image_reader, tf.float32)
dims_expander = tf.expand_dims(float_caster, 0)
resized = tf.image.resize_bilinear(dims_expander, [input_height, input_width])
normalized = tf.divide(tf.subtract(resized, [input_mean]), [input_std])
sess = tf.compat.v1.Session()
result = sess.run(normalized)
return result
def main():
# Loading the Trained Machine Learning Model created from running retrain.py on the training_images directory
graph = load_graph('/tmp/retrain_tmp/output_graph.pb')
labels = load_labels("/tmp/retrain_tmp/output_labels.txt")
# Load up our session
input_operation = graph.get_operation_by_name("import/Placeholder")
output_operation = graph.get_operation_by_name("import/final_result")
sess = tf.compat.v1.Session(graph=graph)
### capteha_api.py
#yourREALemailAddress = "YourRealEmail@SomeRealEmailDomain.RealTLD"
yourREALemailAddress = "mo@.SomeRealEmailDomain.RealTLD.org"
# Creating a session to handle cookies
s = requests.Session()
url = "https://fridosleigh.com/"
print("Sending capteha request...")
json_resp = json.loads(s.get("{}api/capteha/request".format(url)).text)
b64_images = json_resp['images'] # A list of dictionaries eaching containing the keys 'base64' and 'uuid'
challenge_image_type = json_resp['select_type'].split(',') # The Image types the CAPTEHA Challenge is looking for.
challenge_image_types = [challenge_image_type[0].strip(), challenge_image_type[1].strip(), challenge_image_type[2].replace(' and ','').strip()] # cleaning and formatting
print("Challenge types:" + str(challenge_image_types))
# Can use queues and threading to spead up the processing
q = queue.Queue()
unknown_images_dir = 'unknown_images'
unknown_images = os.listdir(unknown_images_dir)
#Going to interate over each of our images.
#for image in unknown_images:
for image in b64_images:
print("img uuid:" + str(image['uuid']))
# https://stackoverflow.com/questions/16214190/how-to-convert-base64-string-to-image
imgdata = base64.b64decode(image['base64'])
#img_full_path = '{}/{}'.format(unknown_images_dir, image)
#print('Processing Image {}'.format(img_full_path))
# We don't want to process too many images at once. 10 threads max
while len(threading.enumerate()) > 10:
time.sleep(0.0001)
#predict_image function is expecting png image bytes so we read image as 'rb' to get a bytes object
#image_bytes = open(img_full_path,'rb').read()
image_bytes = imgdata
#threading.Thread(target=predict_image, args=(q, sess, graph, image_bytes, img_full_path, labels, input_operation, output_operation)).start()
threading.Thread(target=predict_image, args=(q, sess, graph, image_bytes, str(image['uuid']), labels, input_operation, output_operation)).start()
print('Waiting For Threads to Finish...')
while q.qsize() < len(b64_images):
time.sleep(0.001)
#getting a list of all threads returned results
prediction_results = [q.get() for x in range(q.qsize())]
final_answer = ""
#do something with our results... Like print them to the screen.
for prediction in prediction_results:
if any(image_type in str(prediction["prediction"]) for image_type in challenge_image_types):
final_answer = final_answer + str(prediction["img_full_path"]) + ","
print (str(prediction))
print('TensorFlow Predicted {img_full_path} is a {prediction} with {percent:.2%} Accuracy'.format(**prediction) + str(challenge_image_types))
### capteha_api.py
final_answer = final_answer.rstrip(',')
print("final answer:" + final_answer)
# This should be JUST a csv list image uuids ML predicted to match the challenge_image_type .
#final_answer = ','.join( [ img['uuid'] for img in b64_images ] )
json_resp = json.loads(s.post("{}api/capteha/submit".format(url), data={'answer':final_answer}).text)
if not json_resp['request']:
# If it fails just run again. ML might get one wrong occasionally
print('FAILED MACHINE LEARNING GUESS')
print('--------------------\nOur ML Guess:\n--------------------\n{}'.format(final_answer))
print('--------------------\nServer Response:\n--------------------\n{}'.format(json_resp['data']))
sys.exit(1)
print('CAPTEHA Solved!')
# If we get to here, we are successful and can submit a bunch of entries till we win
userinfo = {
'name':'Krampus Hollyfeld',
'email':yourREALemailAddress,
'age':180,
'about':"Cause they're so flippin yummy!",
'favorites':'thickmints'
}
# If we win the once-per minute drawing, it will tell us we were emailed.
# Should be no more than 200 times before we win. If more, somethings wrong.
entry_response = ''
entry_count = 1
while yourREALemailAddress not in entry_response and entry_count < 200:
print('Submitting lots of entries until we win the contest! Entry #{}'.format(entry_count))
entry_response = s.post("{}api/entry".format(url), data=userinfo).text
entry_count += 1
print(entry_response)
if __name__ == "__main__":
main()
You run the combined code, you get the following results:
Kringlecon 2 - Solving CAPTEHA
Kringlecon 2 - CAPTEHA Solved!!
Kringlecon 2 - You won!
After a few minutes you receive this email to notify you of your winning.
Kringlecon 2 - Winner notification.
Objective 8 - Solution¶
Answer:
8Ia8LiZEwvyZr2WO
Objective 9 - Retrieve Scraps of Paper from Server¶
| Inspirational Quote | "If you need answer, talk to a rubber duck!" -kaknowles |
| Objective | Gain access to the data on the Student Portal server and retrieve the paper scraps hosted there. What is the name of Santa's cutting-edge sleigh guidance system? For hints on achieving this objective, please visit the dorm and talk with Pepper Minstix. |
| Difficulty Level: | 4 |
| Links | Student Portal |
| Related Video |
Graylog - Terminal Challenge¶
| Elf Name | Pepper Minstix |
| Pre-Solve Hints | Graylog Docs, (Events and Sysmon) |
| Post-Solve Hints | Sqlmap Tamper Scripts, SQL Injection from OWASP |
| Objective |
Kringlecon 2 - Graylog - Terminal Challenge
You read the Graylog Docs. You start the terminal challenge and login with credential elfustudent/elfustudent. You use various search parameters to find the answers to the questions.
Kringlecon 2 - Graylog Incident Response Report - Terminal Challenge
Graylog - Solution¶
Answer:
ElfU Graylog Incident Response Report
Graylog Login:
elfustudent/elfustudent.
Question 1:
Minty CandyCane reported some weird activity on his computer after he clicked on a link in Firefox for a cookie recipe and downloaded a file.
What is the full-path + filename of the first malicious file downloaded by Minty?
Answer: C:\Users\minty\Downloads\cookie_recipe.exe
Hint: We can find this searching for sysmon file creation event id 2 with a process named firefox.exe and not junk .temp files. We can use regular expressions to include or exclude patterns:
TargetFilename:/.+\.pdf/
Question 2:
The malicious file downloaded and executed by Minty gave the attacker remote access to his machine. What was the ip:port the malicious file connected to first?
Answer: 192.168.247.175:4444
Hint: We can pivot off the answer to our first question using the binary path as our ProcessImage
Question 3:
What was the first command executed by the attacker? (answer is a single word)
Answer: C:\Windows\system32\cmd.exe /c "whoami "
Hint: Since all commands (sysmon event id 1) by the attacker are initially running through the cookie_recipe.exe binary, we can set its full-path as our ParentProcessImage to find child processes it creates sorting on timestamp.
Search: "ParentProcessCommandLine:/.*cookie_recipe.*/"
Question 4:
What is the one-word service name the attacker used to escalate privileges?
Answer: webexservice
Hint: Continuing on using the cookie_reciper.exe binary as our ParentProcessImage, we should see some more commands later on related to a service.
Question 5:
What is the file-path + filename of the binary ran by the attacker to dump credentials?
Answer: C:\cookie.exe
Hint: The attacker elevates privileges using the vulnerable webexservice to run a file called cookie_recipe2.exe. Let's use this binary path in our ParentProcessImage search.
Question 6:
The attacker pivoted to another workstation using credentials gained from Minty's computer. Which account name was used to pivot to another machine?
Answer: alabaster
Hint:Windows Event Id 4624 is generated when a user network logon occurs successfully. We can also filter on the attacker's IP using SourceNetworkAddress.
Search: EventID:4624 AND SourceNetworkAddress:192.168.247.175
Question 7:
What is the time ( HH:MM:SS ) the attacker makes a Remote Desktop connection to another machine?
Answer
Answer: 06:04:28
Hint: LogonType 10 is used for successful network connections using the RDP client.
Search: EventID:4624 AND SourceNetworkAddress:192.168.247.175
Question 8:
The attacker navigates the file system of a third host using their Remote Desktop Connection to the second host. What is the SourceHostName,DestinationHostname,LogonType of this connection? (submit in that order as csv)
Answer: ELFU-RES-WKS2,elfu-res-wks3,3
Search: ventID:4624 AND SourceHostName:ELFU\-RES\-WKS2
Hint:The attacker has GUI access to workstation 2 via RDP. They likely use this GUI connection to access the file system of of workstation 3 using explorer.exe via UNC file paths (which is why we don't see any cmd.exe or powershell.exe process creates). However, we still see the successful network authentication for this with event id 4624 and logon type 3.
Question 9:
What is the full-path + filename of the secret research document after being transferred from the third host to the second host?
Answer: C:\Users\alabaster\Desktop\super_secret_elfu_research.pdf
Hints:
Search EventID:2 AND source:elfu\-res\-wks2 AND NOT TargetFilename:/.+AppData.+/
We can look for sysmon file creation event id of 2 with a source of workstation 2. We can also use regex to filter out overly common file paths using something like:
AND NOT TargetFilename:/.+AppData.+/
Question 10:
What is the IPv4 address (as found in logs) the secret research document was exfiltrated to?
Answer: 104.22.3.84
Hint: We can look for the original document in CommandLine using regex.
When we do that, we see a long a long PowerShell command using Invoke-Webrequest to a remote URL of https://pastebin.com/post.php.
We can pivot off of this information to look for a sysmon network connection id of 3 with a source of elfu-res-wks2 and DestinationHostname of pastebin.com.
Search: pastebin.com
Kringlecon 2 - Report Submission
Message from Pepper Ministix after solving the challenge:
Kringlecon 2 - Graylog Incident Response Report - Terminal Challenge
Objective 9 - Walkthrough¶
You read the hints that were provided from solving the last terminal challenge. You look at the student portal.
Kringlecon 2 - Check Application Status
You try a simple SQL injection 'email@domain.com to ese if the website is vulnerable to SQL injection.
Kringlecon 2 - SQL injection
After reviewing the webpage you notice that the CSRF validaitor url is https://studentportal.elfu.org/validator.php
You download SQLMAP. You use the following configs:
url = https://studentportal.elfu.org/application-check.php?elfmail=test%40test.com&token=
method = get
csrfToken = token
csrfUrl = https://studentportal.elfu.org/validator.php
csrfMethod = GET
verbose = 6
You run SQLMAP with -dump. You get an error message that it's unable to find the CSRF token.
You search github to see where this error is coming from. You notice this error is coming from connect.py file around line 1110.
Kringlecon 2 - Interesting table
You review the code and add 3 lines to "FIX" the code.
print ("page:" +str(page))
token.name="token"
token.value=str(page).replace("=","%3D")
Kringlecon 2 - connect.py "FIX"
You re-run SQLMAP with -dump.
Kringlecon 2 - SQLMAP Running.
SQLMAP finds a database that has 6 image uids.
Kringlecon 2 - Interesting table
Kringlecon 2 - SQLMAP completed.
You download the 6 images that you found in the table.

Kringlecon 2 - 0f5f510e.png

Kringlecon 2 - 1cc7e121.png

Kringlecon 2 - 439f15e6.png

Kringlecon 2 - 667d6896.png

Kringlecon 2 - adb798ca.png

Kringlecon 2 - ba417715.png
You make out the name of Santa's cutting-edge sleigh guidance system on the edges of the scrapes.
Objective 9 - Solution¶
Answer:
Super sled-o-matic
Objective 10 - Recover Cleartext Document¶
| Inspirational Quote | "Solve objectives to unravel the mystery |
| Objective | The Elfscrow Crypto tool is a vital asset used at Elf University for encrypting SUPER SECRET documents. We can't send you the source, but we do have debug symbols that you can use. Recover the plaintext content for this encrypted document. We know that it was encrypted on December 6, 2019, between 7pm and 9pm UTC. What is the middle line on the cover page? (Hint: it's five words) For hints on achieving this objective, please visit the NetWars room and talk with Holly Evergreen. |
| Difficulty Level: | 5 |
| Links | Elfscrow Crypto, debug symbols, encrypted document |
| Related Video | Ron Bowes, Reversing Crypto the Easy Way |
Mongo Pilfer - Terminal Challenge¶
| Elf Name | Holly Evergreen |
| Pre-Solve Hints | MongoDB Documentation |
| Post-Solve Hints | Reversing Crypto the Easy Way |
| Objective |
Kringlecon 2 - Holy Evergreen - Terminal Challenge
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
You read the hint provided by Holly Evergreen. You open the Mongo Pilfer terminal.
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
You run mongo and receive this error message.
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
You notice Mongo is not running on a default port.
You look around and find a file in the root go.sh.
Kringlecon 2 - cat /go.sh
This file shows that mongo is running on port 12121.
You run mongo localhost:12121 to connect to the mongo server.
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
You run show dbs to get a list of databases. You switch to elfu database. You list the collections show collections.
You run the action find on collection solution.
You run the command that is displayed from the above command.
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
Mongo Pilfer - Solution¶
Answer:
mongo localhost:12121
db.loadServerScripts();displaySolution();
Message from Holly Evergreen after solving the challenge:
Kringlecon 2 - Mongo Pilfer - Terminal Challenge
Objective 10 - Walkthrough¶
You watch the Reversing Crypto the Easy Way.
You run elfscrow.exe in a sandbox and encrypt a test document. You notice each time the document is encrypted it is providing a different escrow key.
You start by downloading and installing the free version of IDA. You download the symbols provided in the challenge. You open elfscrow.exe in IDA and load the symbols.
You navigate to generate_key function. You notice the function is calling the time. After the time function has been called it's calling the super_secure_srand function.
Kringlecon 2 - Ida Generate_key function
You google the time function and notice that it returns the time in epoch.
Kringlecon 2 - time function
You write a python program to output time in epoch.
import time
i=1
while i < 100:
seconds = int(time.time())
print("Seed =", seconds)
i += 1
You run elfscrow.exe at the same time as the python script and confirm that elfscrow.exe is using is time() as the Seed.
Kringlecon 2 - Elfscrow.exe
From earlier, you know this seed is likely passed to super_secure_srand function.
You review super_secure_srand.
Kringlecon 2 - super_secure_srand function
You see a few constant in this function, ex. 2531011.
You search Google for this constant. You find a Fastrand() function that uses the same constants.
Kringlecon 2 - Fastrand()
You remember the video talked about how to create a generate_key function.
Kringlecon 2 - Screenshot from the talk
Using the video as a guide, you write the generate_key() function.
def generate_key(seed):
key=""
for i in range(8):
seed=(214013*seed + 2531011)
key += chr(((seed >> 16)&0x7fff)&0x0ff)
return key
While reviewing the code, you find that the encryption is likely DES-CBC.
Kringlecon 2 - DES-CBC key
You test decrypting the file you encrypted on CyberChef.
Kringlecon 2 - Decrypt the file encrypted by elfscrow.exe
The objective states the file was encrypted on December 6, 2019, between 7pm and 9pm UTC. You convert the time to epoch time.
Kringlecon 2 - epoch time December 6, 2019, 7 PM
Kringlecon 2 - epoch time December 6, 2019, 9 PM
You know the key is between 1575658800 and 1575666000.
You write a For loop around generate_key() function to generate all the keys. You output all the keys to a keys.txt.
You download CyberChef API from github.
You write a wrapper in Javascript to open keys.txt and decrypt it using CyberChef framework. You use the DES-CBC to decrypt the ElfUResearchLabsSuperSledOMaticQuickStartGuideV1.2.pdf.enc with all possible keys. You output the decrypted files to a folder with the key that was used to decrypt it as the filename.
{% highlight JavaScript linenos %} // app.js const chef = require("cyberchef"); var readline = require('readline'); const fs = require('fs');
let file = fs.readFileSync("ElfUResearchLabsSuperSledOMaticQuickStartGuideV1.2.pdf.enc"); console.log(file) ;
var myInterface = readline.createInterface({ input: fs.createReadStream('keys.txt') });
var lineno = 0; myInterface.on('line', function (line) { lineno++; console.log('Line number ' + lineno + ': ' + line.trim());
try {
var results = chef.DESDecrypt(file,{
Key:{string:line.trim(), option:"Hex"},
IV:{string:"0000000000000000", option:"Hex"},
Mode: "CBC",
Input:"Raw",
Output:"Raw"},).toString();
// console.log(results);
fs.writeFileSync('./files/'.concat(line.trim()), results, "binary",(err) => {
// throws an error, you could also catch it here
if (err) throw err;
// success case, the file was saved
console.log('Lyric saved!');
});
results = ''
}
catch(err) {
}
});
{% endhighlight JavaScript %}
You run the JavaScript file and wait until it has decrypted the file with all possible keys.
Once completed, you run the command grep -rl "%PDF" to find the decrypted file that has a PDF header.
Kringlecon 2 - The only decrypted file with the "%PDF" header
The key used to encrypt the file is b5ad6a321240fbec.
You open the decrypted file.
Kringlecon 2 - Document decrypted
You notice an interesting section in the file that may come handy later.
Kringlecon 2 - Document decrypted
Objective 10 - Solution¶
Answer:
Machine Learning Sleigh Route Finder
Objective 11 - Open the Sleigh Shop Door¶
| Inspirational Quote | "You must learn to say 'no'" -hacks4pancake |
| Objective | Visit Shinny Upatree in the Student Union and help solve their problem. What is written on the paper you retrieve for Shinny? For hints on achieving this objective, please visit the Student Union and talk with Kent Tinseltooth. |
| Difficulty Level: | 5 |
| Links | Crate |
| Related Video | |
Smart Braces - Terminal Challenge¶
| Elf Name | Kent Tinseltooth |
| Pre-Solve Hints | Iptables |
| Post-Solve Hints | Chrome Dev Tools |
| Objective |
Kringlecon 2 - Kent Tinseltooth - Terminal Challenge
You open the console and see the following messages:
Kringlecon 2 - Smart Braces - Terminal Challenge
You read IOTteethBraces.md.
Kringlecon 2 - IOTteethBraces.md
This is a timed challenge. If you take too long to solve the challenge, you're greeted with the following message:
Kringlecon 2 - Kent Tinseltooth - Terminal Challenge
You read the hint for this challenge and write the IP tables for the challenge.
Kringlecon 2 - Kent Tinseltooth - Terminal Challenge
Smart Braces - Solution¶
Answer:
sudo iptables -F
sudo iptables -P FORWARD DROP
sudo iptables -P INPUT DROP
sudo iptables -P OUTPUT DROP
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
sudo iptables -A OUTPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
sudo iptables -A INPUT -p tcp -s 172.19.0.255 --dport 22 -j ACCEPT
sudo iptables -A INPUT -p tcp --match multiport --dport 21,80 -j ACCEPT
sudo iptables -A OUTPUT -p tcp --dport 80 -j ACCEPT
sudo iptables -A INPUT -i lo -j ACCEPT
Message from Kent Tinseltooth after solving the challenge:
Kringlecon 2 - Kent Tinseltooth - Terminal Challenge
Objective 11 - Walkthrough¶
You visit Shinny Upatree and are greeted with this message:
Kringlecon 2 - Shinny Upatree
When you visit crate website, you're greeted with a number of locks that you have to open. Each lock provides hint(s) for opening the lock.
Lock 1¶
You open the chrome developer tools and see a code 62ID5140. You type this code in lock 1 and it unlocks.
Kringlecon 2 - Lock 1
Lock 2¶
You proceed to lock 2.
Kringlecon 2 - Lock 2
You view the source code for lock 2 and see the code 5U7A9BBX.
Kringlecon 2 - Lock 2 Source Code
Kringlecon 2 - Lock 2 - Print Preview
Lock 3¶
You proceed to lock 3.
Kringlecon 2 - Lock 3
You view the Network response in chrome developer tools.
Kringlecon 2 - Lock 3 - Network response
You load the .png file that you see in network response.
Kringlecon 2 - Lock 3 - png
You type the code in lock 3 to unlock it.
Kringlecon 2 - Lock 3 - Solved
Lock 4¶
You proceed to lock 4.
Kringlecon 2 - Lock 4
You go to Application tab in chrome developer tools and expand Local Stroage under Storage.
Kringlecon 2 - Lock 4 - Local Storage
You type the code to unlock lock 4.
Kringlecon 2 - Lock 4 - Solved
Lock 5¶
You proceed to Lock 5.
Kringlecon 2 - Lock 5
The hint says to view the title on the html page. You view the title.
Kringlecon 2 - Lock 5 - html
You type the code in lock 5 to unlock it.
Kringlecon 2 - Lock 5 - Solved
Lock 6¶
You proceed to Lock 6.
Kringlecon 2 - Lock 6
You view the .css file and update the perspective variable.
Kringlecon 2 - Lock 6 - .css
The code becomes visible.
Kringlecon 2 - Lock 6 - .css
You type the code in the lock.
Lock 7¶
You proceed to Lock 7.
Kringlecon 2 - Lock 7
You view the font-family in the html file and see QCIAX2SW
Kringlecon 2 - Lock 7 - font-family html
You type the code to unlock lock 7.
Lock 8¶
You proceed to Lock 8
Kringlecon 2 - Lock 8
Kringlecon 2 - Lock 8 - Code analysiss
You create a button .egg and get the event listener.
Kringlecon 2 - Lock 8 - Event Listener
You enter VERONICA into the lock to unlock it.
Lock 9¶
You proceed to lock 9.
Kringlecon 2 - Lock 9
You set the chakra's in the code to active. You see that the code appears above the instructions.
Kringlecon 2 - Lock 9
You type the code into the lock to unlock.
Kringlecon 2 - Lock 9 - Solved
Lock 10¶
You proceed to lock 10.
Kringlecon 2 - Lock 10
You view the code for the lock.
Kringlecon 2 - Lock 10 - Code
You remove the "cover".
Kringlecon 2 - Lock 10 - Remove Cover
Kringlecon 2 - Lock 10
When you try to type a code the lock, an error appears in the console that it's missing a macaroni. You search the code for macaroni and find this.
Kringlecon 2 - Lock 10 - macaroni
You look at the .css and find that there is a mac.png, qtip.png and gnome.png.
Kringlecon 2 - Lock 10 - png, qtip.png and gnome.png
You look for gnome in the code.
Kringlecon 2 - Lock 10 - gnome
You find swab in the code.
Kringlecon 2 - Lock 10 - swab/qtip
You copy the three components to the lock 10 code.
Kringlecon 2 - Lock 10 - Fix circuit board
Kringlecon 2 - Lock 10 - Fixed lock
You zoom into the side of the circuit board to find the code to unlock the lock K029XJ37.
Kringlecon 2 - Lock 10 - code
You're greeted by this message once you unlock lock 10.
Kringlecon 2 - Lock 10 - code
Objective 11 - Solution¶
Answer:
Lock 1: 62ID5140
Lock 2: 5U7A9BBX
Lock 3: FZUNIJFD
Lock 4: H0UHDN8S
Lock 5: ZW5698HD
Lock 6: SRB40Q5Q
Lock 7: QCIAX2SW
Lock 8: VERONICA
Lock 9: 0QIMRKYC
Lock 10: K029XJ37
The villian is The Tooth Fairy.
Objective 12 - Filter Out Poisoned Sources of Weather Data¶
| Inspirational Quote | "A Nerarious, villainous, Evil attacker is the worst of attacker you can have." -Ed Skoudis |
| Objective | Use the data supplied in the Zeek JSON logs to identify the IP addresses of attackers poisoning Santa's flight mapping software. Block the 100 offending sources of information to guide Santa's sleigh through the attack. Submit the Route ID ("RID") success value that you're given. For hints on achieving this objective, please visit the Sleigh Shop and talk with Wunorse Openslae. |
| Difficulty Level: | 4 |
| Links | Zeek JSON logs, Block the 100 offending sources of information to guide Santa's sleigh |
| Related Video |
Zeek JSON Analysis - Terminal Challenge¶
| Elf Name | Wunorse Openslae |
| Pre-Solve Hints | Parsing Zeek JSON Logs with JQ |
| Post-Solve Hints | Do you see any LFI, XSS, Shellshock, or SQLi? |
| Objective |
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
You read the instructions for jq. You open the terminal console.
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
You use jq to find the longest durations.
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
You modify the query to display the host and destinations.
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
You modify the query to sort by duration and get the last item of the list.
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
You run the runtoanswer and type in 13.107.21.200.
Kringlecon 2 - Zeek JSON Analysis - Terminal Challenge
Zeek JSON Analysis - Solution¶
Answer:
13.107.21.200
Message from Wunorse Openslae after solving the challenge:
Kringlecon 2 - Wunorse Openslae - Terminal Challenge
Objective 12 - Walkthrough¶
You download zeek logs. We need to find the credentials to login to the website.
You use JQ to filter out the noise and view successful connections.
jq '.[] | select (.uri | contains ("weather?station") | not) | select (.status_code == 200) | .uri' http.log | sort |uniq
Kringlecon 2 - Filter out the noise using JQ
You see a file name README.md. You remember the document you decrypted in an earlier challenge, referred to default credentials being stored in README.md.
You access srf.elfu.org/README.md.
Kringlecon 2 - README.md
You login srf.elfu.org with the default login.
Kringlecon 2 - srf login page
The welcome page once you login to srf.
Kringlecon 2 - srf welcome page
You review the Firewall instructions on how to block and allow IPs.
Kringlecon 2 - Firewall Instructions
You use JQ and the hints to find some of the bad IPs:
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host , "\n"' http.log | grep -E \' > blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | awk '/\/\.\./' >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep -E "\.\." >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep -E \/\.\% >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep pass >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep \> >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep \& >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | grep \| >> blah.csv
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | awk '/\;\s*\}/' >> blah.csv
From the above queries you get 78 Bad IPs. You know there is about 100 bad IPs. You export all the events to a .csv file.
jq -j '.[] | .["id.orig_h"], ", ",.["user_agent"],", ", .uri, ", ",.username, ", ",.password, ", ",.host, "\n"' http.log | > all.csv
You open all.csv in excel and look at the data.
Kringlecon 2 - Pivot table on the User-Agent
You use vlookup to get the user-agent count for each of the IP's user-agents. You filter on user-agent count that are low. You filter out the IPs that are already in your bad IP list.
Kringlecon 2 - Filter by user-agents that have low hits.
You get about 39 new IPs.
103.235.93.133
118.26.57.38
44.164.136.41
249.237.77.152
203.68.29.5
10.122.158.57
187.152.203.243
50.154.111.0
217.132.156.225
252.122.243.212
29.0.183.220
22.34.153.164
66.116.147.181
126.102.12.53
31.116.232.143
250.22.86.40
140.60.154.239
226.102.56.13
42.127.244.30
104.179.109.113
42.103.246.130
42.103.246.130
42.103.246.130
42.103.246.130
185.19.7.133
42.16.149.112
158.171.84.209
34.155.174.167
249.90.116.138
231.179.108.238
92.213.148.0
97.220.93.190
87.195.80.126
53.160.218.44
253.65.40.39
226.240.188.154
148.146.134.52
142.128.135.10
37.216.249.50
You combine the bad IPs. Here is a list of bad IPs:
42.103.246.250,49.161.8.58,84.147.231.129,2.230.60.70,10.155.246.29,225.191.220.138,75.73.228.192,249.34.9.16,27.88.56.114,238.143.78.114,121.7.186.163,106.132.195.153,129.121.121.48,190.245.228.38,34.129.179.28,135.32.99.116,2.240.116.254,45.239.232.245,33.132.98.193,84.185.44.166,254.140.181.172,150.50.77.238,68.115.251.76,118.196.230.170,173.37.160.150,81.14.204.154,135.203.243.43,186.28.46.179,13.39.153.254,111.81.145.191,0.216.249.31,220.132.33.81,83.0.8.119,150.45.133.97,229.229.189.246,227.110.45.126,123.127.233.97,80.244.147.207,200.75.228.240,230.246.50.221,223.149.180.133,187.178.169.123,116.116.98.205,102.143.16.184,52.39.201.107,131.186.145.73,253.182.102.55,1.185.21.112,229.133.163.235,194.143.151.224,23.49.177.78,75.215.214.65,211.229.3.254,250.51.219.47,180.57.20.247,9.206.212.33,79.198.89.109,25.80.197.172,193.228.194.36,169.242.54.5,28.169.41.122,233.74.78.199,132.45.187.177,56.5.47.137,19.235.69.221,69.221.145.150,42.191.112.181,48.66.193.176,44.74.106.131,106.93.213.219,31.254.228.4,61.110.82.125,65.153.114.120,95.166.116.45,168.66.108.62,139.45.221.220,96.156.113.98,170.51.98.223,103.235.93.133,118.26.57.38,44.164.136.41,249.237.77.152,203.68.29.5,10.122.158.57,187.152.203.243,50.154.111.0,217.132.156.225,252.122.243.212,29.0.183.220,22.34.153.164,66.116.147.181,126.102.12.53,31.116.232.143,250.22.86.40,140.60.154.239,226.102.56.13,42.127.244.30,104.179.109.113,42.103.246.130,185.19.7.133,42.16.149.112,158.171.84.209,34.155.174.167,249.90.116.138,231.179.108.238,92.213.148.0,97.220.93.190,87.195.80.126,53.160.218.44,253.65.40.39,226.240.188.154,148.146.134.52,142.128.135.10,37.216.249.50
You block the IPs on the firewall.
Kringlecon 2 - Block bad IPs in firewall
Objective 12 - Solution¶
Answer:
Route Calculation Success! RID:0807198508261964
Message from Tooth Fairy after solving the challenge:
Kringlecon 2 - Tooth Fairy response
Conclusion¶
Once you solve the challenge, the bell tower door opens up.
Kringlecon 2 - Bell Tower Access
You go up the ladder to the bell tower.
Kringlecon 2 - Bell Tower Access
You open the letter in the corner of the room.
Kringlecon 2 - Bell Tower
You talk to Santa.
Kringlecon 2 - Santa
You talk to Tooth Fairy.
Kringlecon 2 - Tooth Fairy
You talk to Krampus.
Kringlecon 2 - Krampus
The narrative of the story line:
Whose grounds these are, I think I know
His home is in the North Pole though
He will not mind me traipsing here
To watch his students learn and grow
Some other folk might stop and sneer
"Two turtle doves, this man did rear?"
I'll find the birds, come push or shove
Objectives given: I'll soon clear
Upon discov'ring each white dove,
The subject of much campus love,
I find the challenges are more
Than one can count on woolen glove.
Who wandered thus through closet door?
Ho ho, what's this? What strange boudoir!
Things here cannot be what they seem
That portal's more than clothing store.
Who enters contests by the ream
And lives in tunnels meant for steam?
This Krampus bloke seems rather strange
And yet I must now join his team...
Despite this fellow's funk and mange
My fate, I think, he's bound to change.
What is this contest all about?
His victory I shall arrange!
To arms, my friends! Do scream and shout!
Some villain targets Santa's route!
What scum - what filth would seek to end
Kris Kringle's journey while he's out?
Surprised, I am, but "shock" may tend
To overstate and condescend.
'Tis little more than plot reveal
That fairies often do extend
And yet, despite her jealous zeal,
My skills did win, my hacking heal!
No dental dealer can so keep
Our red-clad hero in ordeal!
This Christmas must now fall asleep,
But next year comes, and troubles creep.
And Jack Frost hasn't made a peep,
And Jack Frost hasn't made a peep...